MOTOSHARE 🚗🏍️
Turning Idle Vehicles into Shared Rides & Earnings
From Idle to Income. From Parked to Purpose.
Earn by Sharing, Ride by Renting.
Where Owners Earn, Riders Move.
Owners Earn. Riders Move. Motoshare Connects.
With Motoshare, every parked vehicle finds a purpose.
Owners earn. Renters ride.
🚀 Everyone wins.
What is Cryptography?
Cryptography is the practice of securing information by transforming it into a format that is unreadable to unauthorized individuals while allowing authorized parties to access and interpret the data. It encompasses various techniques used to protect the confidentiality, integrity, authentication, and non-repudiation of data. At its core, cryptography is the science of using mathematical algorithms to convert data into an encrypted form (ciphertext) and, if necessary, back into its original form (plaintext).
In modern technology, cryptography plays a crucial role in securing digital communications, online transactions, and protecting sensitive information from cyber threats.
Key Aspects of Cryptography:
- Encryption: The process of converting readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic key.
- Decryption: The reverse process, where the encrypted data is transformed back into its original, readable form using a decryption key.
- Keys: Cryptography relies on the use of keys, which are used for both encryption and decryption. There are two primary types:
- Symmetric key encryption (same key for encryption and decryption)
- Asymmetric key encryption (uses a pair of public and private keys)
- Hash Functions: These are used to create a fixed-size value (hash) from input data. Hash functions are essential in ensuring data integrity.
- Digital Signatures: A way of ensuring data authenticity by associating a unique identifier with the sender of the message, confirming that the data came from the expected source.
What Are the Major Use Cases of Cryptography?
Cryptography is fundamental to modern cybersecurity and has a wide range of applications in various industries. Here are some of the major use cases of cryptography:
1. Secure Communication:
- Use Case: Cryptography is widely used in secure communication systems to prevent unauthorized access to sensitive messages and ensure confidentiality.
- Example: Encrypted email systems, secure messaging apps, and VPNs.
- Why Cryptography? It ensures that communication between parties remains private, preventing eavesdropping by third parties.
2. Data Protection:
- Use Case: Cryptography is used to protect sensitive data stored in systems or transmitted over the internet from being accessed or tampered with.
- Example: File encryption, disk encryption, and cloud storage security.
- Why Cryptography? It secures stored data in case of breaches and ensures that only authorized individuals can access it.
3. Digital Signatures and Authentication:
- Use Case: Cryptography enables digital signatures, which verify the authenticity of digital documents and provide non-repudiation, ensuring that the sender cannot deny sending the data.
- Example: Secure online banking transactions, contract signing, and document verification.
- Why Cryptography? Digital signatures authenticate the identity of the sender, ensuring data integrity and confirming that the content has not been altered.
4. Online Banking and Financial Transactions:
- Use Case: Cryptography secures online transactions, ensuring that financial information such as credit card numbers, account details, and transaction records are kept confidential.
- Example: Credit card transactions, digital wallets, and online payments.
- Why Cryptography? It protects sensitive financial data from theft and fraud during transmission over the internet.
5. Blockchain and Cryptocurrencies:
- Use Case: Cryptography is at the core of blockchain technology, ensuring the security and integrity of transaction data in cryptocurrencies like Bitcoin and Ethereum.
- Example: Cryptocurrency transactions, smart contracts, and blockchain verification.
- Why Cryptography? Blockchain uses cryptographic principles to maintain a decentralized and tamper-resistant ledger of transactions.
6. Secure Voting Systems:
- Use Case: Cryptography is used to secure electronic voting systems, ensuring that votes are cast securely, remain confidential, and cannot be tampered with.
- Example: E-voting systems used in elections.
- Why Cryptography? It ensures the integrity and privacy of voting processes, making them resistant to manipulation and fraud.
7. Integrity and Authentication in Software:
- Use Case: Cryptography is used to verify the integrity of software, ensuring that applications or files have not been tampered with or corrupted.
- Example: Software updates, file integrity checks, and digital certificates.
- Why Cryptography? Hash functions and digital signatures can detect changes in software, ensuring the authenticity and integrity of data and files.
How Cryptography Works Along with Architecture?
Cryptography integrates closely with various architectural components of information systems. The way cryptographic operations are implemented depends on whether symmetric or asymmetric encryption is being used.
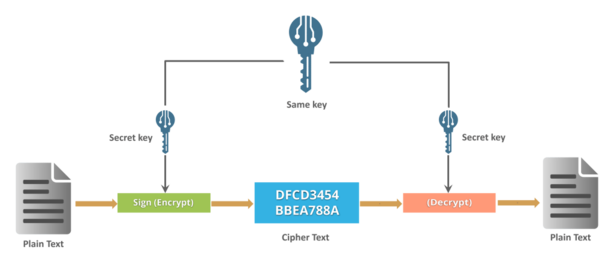
1. Symmetric Key Encryption:
- Architecture: In symmetric encryption, both the sender and receiver use the same key to encrypt and decrypt the data. The security of this system depends on keeping the key secret and securely exchanging the key between parties.
- Example: AES (Advanced Encryption Standard), DES (Data Encryption Standard).
- Process:
- Data is encrypted using a shared key.
- The encrypted data is sent to the receiver.
- The receiver uses the same key to decrypt the data.
2. Asymmetric Key Encryption:
- Architecture: Asymmetric encryption uses a pair of keys: a public key (known to everyone) and a private key (kept secret). The public key is used to encrypt data, while the private key is used to decrypt it. This system is widely used in systems where secure key exchange is required without prior sharing.
- Example: RSA encryption, ECC (Elliptic Curve Cryptography).
- Process:
- The sender uses the recipient’s public key to encrypt the data.
- The recipient uses their private key to decrypt the data.
3. Hash Functions and Integrity Checks:
- Architecture: Hash functions map input data (of any size) to a fixed-size value (hash). These are used to verify the integrity of data by comparing hash values before and after transmission.
- Example: SHA (Secure Hash Algorithm), MD5.
- Process:
- A hash is generated for the original data.
- When the data is transmitted, a hash is generated on the receiving end.
- If the hashes match, the data is verified as unaltered.
4. Digital Signatures:
- Architecture: Digital signatures combine asymmetric encryption and hashing to verify both the origin and integrity of data.
- Example: RSA, ECDSA (Elliptic Curve Digital Signature Algorithm).
- Process:
- The sender hashes the message and encrypts the hash with their private key to create a signature.
- The receiver decrypts the signature using the sender’s public key and compares it with their own hash of the data.
5. SSL/TLS and Secure Communication:
- Architecture: SSL (Secure Sockets Layer) and TLS (Transport Layer Security) use asymmetric encryption (for the exchange of keys) and symmetric encryption (for encrypting the actual data) to establish secure communication channels.
- Example: HTTPS for secure web browsing, VPNs for secure internet access.
- Process:
- The client and server exchange public keys to establish a secure channel.
- Once the channel is established, symmetric encryption is used to encrypt the data transmitted.
What Are the Basic Workflow of Cryptography?
The basic workflow of cryptography typically involves several phases, depending on the type of encryption or security mechanism being used. Below is a simplified workflow:
1. Key Generation:
- Symmetric encryption: A single key is generated and shared between the communicating parties.
- Asymmetric encryption: A pair of keys (public and private) is generated.
- Digital signatures: The signing party generates a private key for signing the data and a corresponding public key for verification.
2. Data Encryption:
- Data is encrypted using the appropriate encryption algorithm, whether it is symmetric (e.g., AES) or asymmetric (e.g., RSA).
- The encrypted data is transformed into ciphertext, which is unreadable to unauthorized parties.
3. Transmission:
- The encrypted data (ciphertext) is transmitted over an insecure medium (e.g., the internet).
- If necessary, additional integrity checks (e.g., hashing) are performed to ensure that the data has not been tampered with during transmission.
4. Data Decryption:
- The recipient uses the appropriate key (e.g., the private key for asymmetric encryption) to decrypt the ciphertext back into the original plaintext.
- If using symmetric encryption, the same key is used by both the sender and receiver to perform encryption and decryption.
5. Authentication and Integrity:
- Digital signatures: The recipient uses the sender’s public key to verify the authenticity of the message and ensure that it has not been altered.
- Hashing: The recipient generates a hash of the received data and compares it with the transmitted hash to ensure integrity.
Step-by-Step Getting Started Guide for Cryptography
Follow these steps to get started with cryptography:
Step 1: Understand the Basics of Cryptography
- Learn the basic concepts, such as encryption, decryption, public and private keys, hashing, and digital signatures.
Step 2: Learn Common Algorithms
- Study popular cryptographic algorithms, such as AES (symmetric encryption), RSA (asymmetric encryption), and SHA-256 (hashing).
Step 3: Choose the Right Cryptographic Tools
- Select the appropriate cryptographic libraries or tools based on your application’s requirements.
- Example Tools: OpenSSL, PyCryptodome (Python), BouncyCastle (Java), and Libsodium (cross-platform).
Step 4: Implement Basic Encryption and Decryption
- Write code that implements basic encryption and decryption using symmetric and asymmetric algorithms.
- Example (Python):
from Crypto.PublicKey import RSA
from Crypto.Cipher import AES
Code language: JavaScript (javascript)Step 5: Use Digital Signatures and Hashing
- Implement digital signatures for verifying data authenticity and hashing for ensuring data integrity.
Step 6: Test and Secure the Application
- Test your implementation to ensure data is being securely encrypted, decrypted, and transmitted without vulnerabilities.
- Apply best practices for key management and secure storage of cryptographic keys.
