Why should I learn AWS?
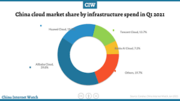
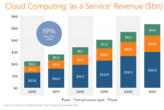
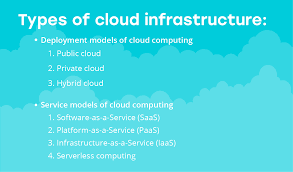
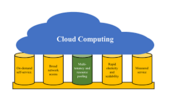
Hello people, today’s article is based on “why should I learn AWS” first of all we will discuss here that what AWS is, why is it important to us, how does it works, why should we learn AWS and last but not the least we will discuss the benefits of AWS. So, without wasting any time let’s start with our today’s article… What is AWS? The AWS is a complete, developing and cloud computing platform that is delivered by Amazon
Read more