Automation in SOAR Goes Further with DevSecOps
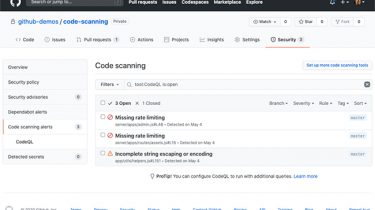
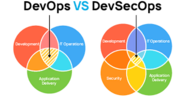
Source:-https://securityboulevard.com Security teams are longing for automation capabilities. And, in recent years, their options have improved with Security Orchestration, Automation and Response (SOAR) and other security solutions like Security Information and Event Management (SIEM), Identity and Access Management (IAM), Endpoint Detection and Response (EDR), and Cloud Detection and Response (CDR) offering automation in a narrow capacity. A recent RSAC blog post suggested that SOAR, because of its likeness to infrastructure as code, is equal to DevSecOps. The article points out
Read more